Standards vs Regulations: What is the difference?
Within the private sector, the industry is structuring itself with cybersecurity standards based on an international consensus from experts from industry, academia and government with the aim to manage new forms of risks and to complement future regulations. Standards are usually introduced by working groups and sponsored by public or non-profit organisations like ETSI, NIST, ANSI, IETF, OWASP and so on, or private standards bodies, such as the internationally recognized standard ISO and the European recognised EN standard. Compliance with a standard is usually voluntary enabling businesses to ensure their products comply with specific market or other contractual requirements.
Within the industry in general there are a lot of cybersecurity standards, take ETSI EN 303 645 as an example. It is designed to prevent large-scale, prevalent attacks against smart devices by establishing a security baseline and building security into products by design. This globally applicable standard targets consumer IoT devices like connected children’s toys and baby monitors, smoke detectors, door locks and other connected safety devices, TVs and speakers, smart wearables, connected appliances, and smart home assistants. Of the 13 recommendations, the top three are: no default passwords, implement a vulnerability disclosure policy, and keep software updated.
Like EN 303 645, the ISA/IEC 66243 standards give guidance on ensuring the safety, integrity, and security of products throughout their lifecycle but for automation and control systems. By defining common terms, concepts and models, asset owners can determine the level of security required to meet their own business and risk needs. It helps establish a cybersecurity lifetime methodology for product developers, including a mechanism to certify products, and risk assessment and vendor development processes.
Regulations, on the other hand, are implemented by the public sector to enforce measures that improve the cybersecurity of the nations. In essence, they are mandatory rules made by a government or other governmental authorities made to control the way things are done or the way people behave to mitigate cybersecurity risks. In the context of the EU Cyber Resilience Act, it is applied in its entirety across all EU member states. Conversely, a directive sets out goals and lets each country devise its own laws.
There is some interplay between standards and regulations. Standards are used as guidelines for organisations that are regulated. They can provide some methodology, organisational measures, technical requirements that can help a company to prove its conformance to regulations. In addition, already existing standards can influence the content of upcoming regulations by setting foundations and expressing a consensus on a subject. Indeed, for the EU Cyber Resilience Act, it may hint at certain existing cybersecurity standards or perhaps replicate them entirely.
Examples of EU regulations that exist today include the most well-known one GDPR, the General Data Protection Regulation, which has been in place since 2018. By itself it is not a cybersecurity regulation but there is the obligation to protect the personal data that has been collected. The NIS2 Directive, or Network Information and Systems Directive, is the first EU-wide cybersecurity regulation applied to digital service providers and operators of essential services. The regulation imposes concrete requirements for cybersecurity to prevent security incidents and makes their reporting mandatory.
On the other hand, there is the Radio Equipment Directive (RED) that was initially just a regulatory framework to ensure that there was no interference between radio emissions of radio equipment placed on the EU market. More recently, in 2019, high-level cybersecurity requirements were added to RED. What’s interesting is that this is the first cybersecurity directive that targets products and not services.
![Cyber Resilience Act in practice Cyber Resilience Act in practice]()
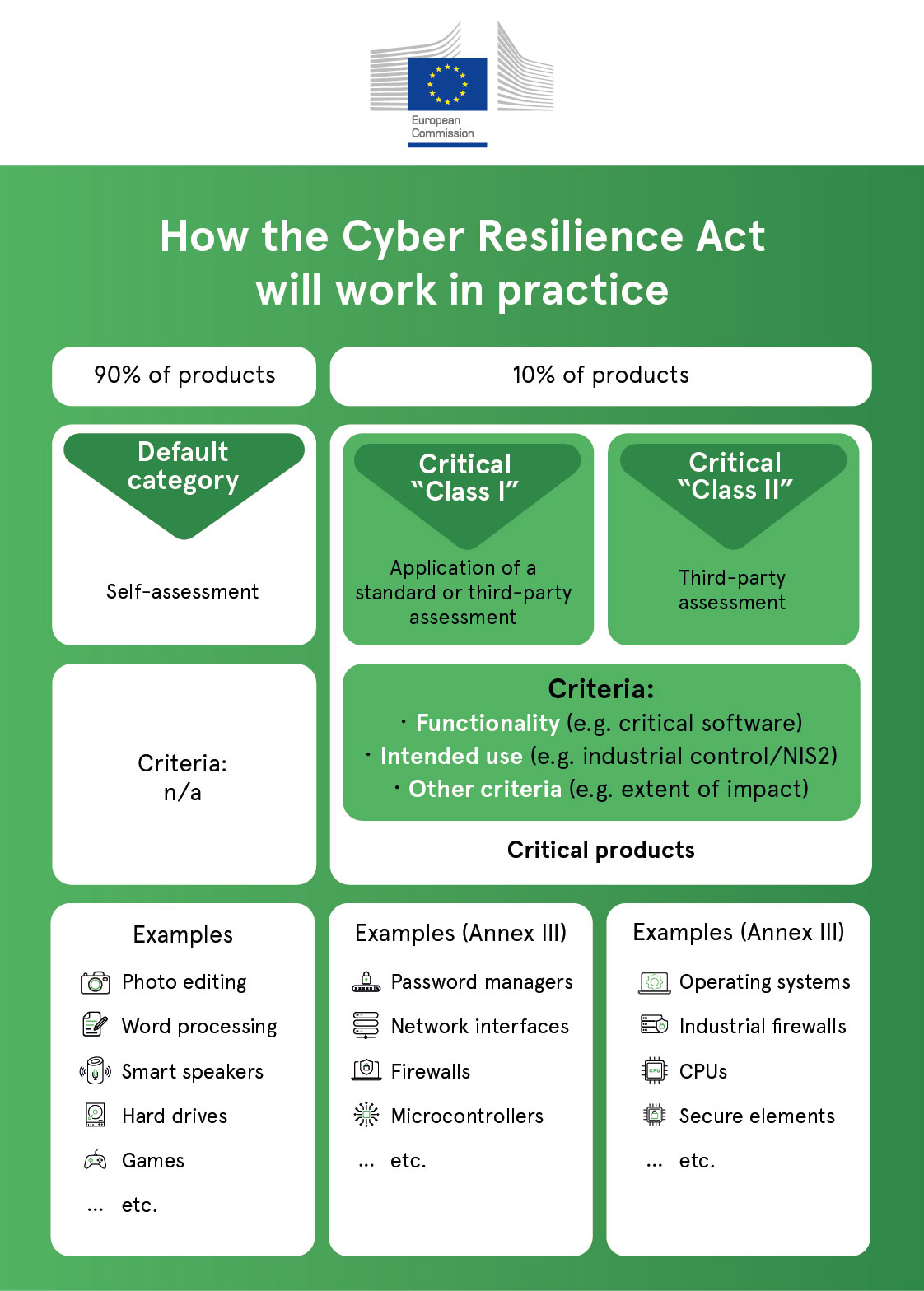
The CRA in practice
The proposed regulation of the EU Cyber Resilience Act targets all products with a digital element, covering both software and hardware. It, therefore, has a broader scope compared to RED and it is probable that it will have stronger cybersecurity requirements.
Overview of the EU Cyber Resilience Act
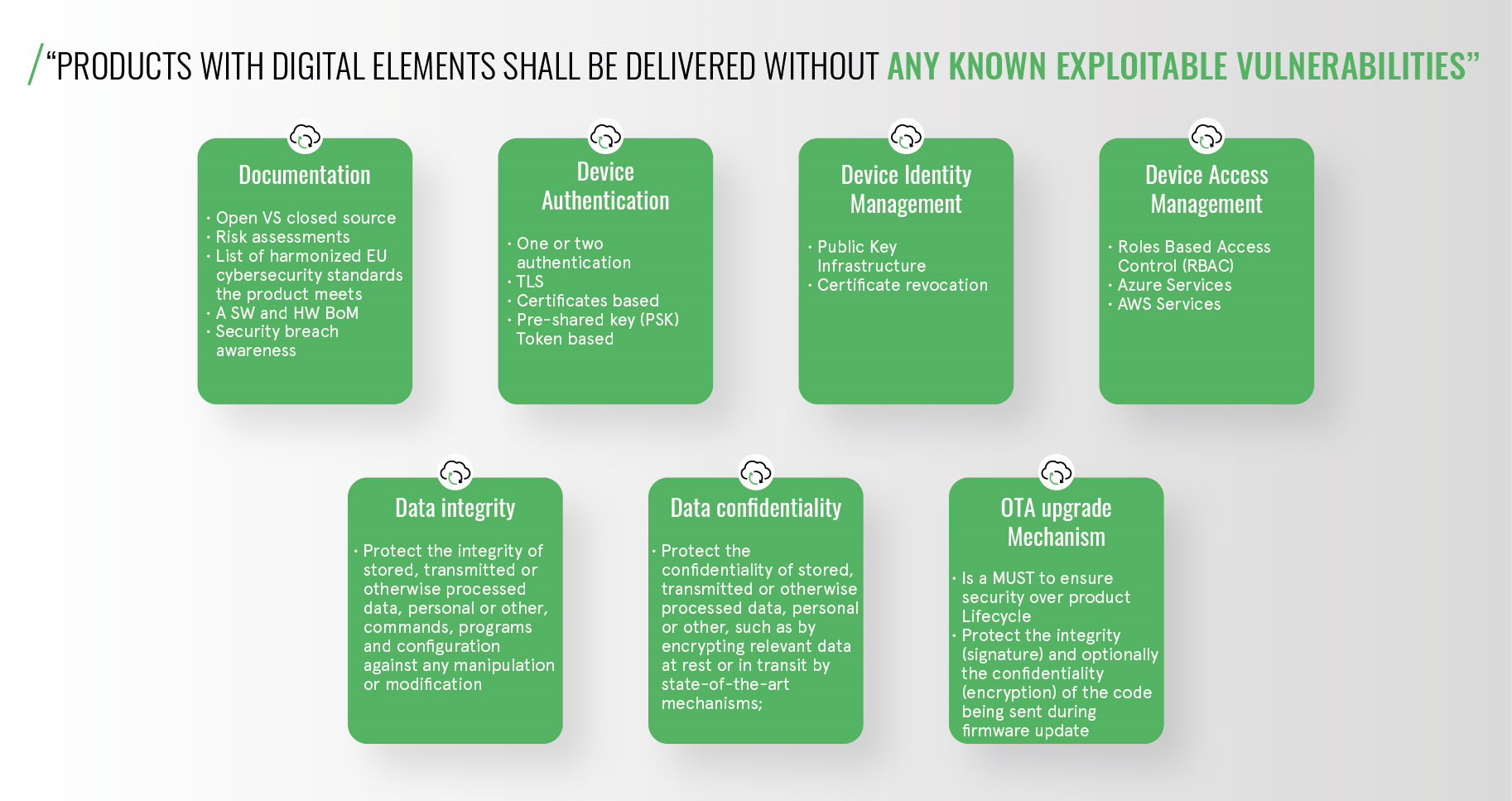
The Cyber Resilience Act is a legal framework that describes the cybersecurity requirements of both hardware and software products with digital elements that shall be placed on the EU market without any known exploitable vulnerabilities and must ensure security for the whole of the product’s lifecycle.
One of the main impacts of the Cyber Resilience Act is that manufacturers are now legally obliged to document everything about the product, including a definition and explanation about the software and hardware bill of materials (BoM). They must also document a detailed list of all the harmonised EU cybersecurity standards that the product meets and perform thorough risk assessments for the OEM and the end-user to better understand the product. In addition, they need to explain which software they are using (open versus closed source) and ensure that they provide the market with ongoing security breach awareness throughout the lifetime of the product.
The other building block that has a significant impact on manufacturers is the over-the-airway (OTA) upgrade mechanism. This capability is a must for two reasons: firstly, the OEM needs to ensure the product’s security for its entire lifecycle. They also need to improve the security features on their product during its lifecycle. Obviously, the OTA upgrade mechanism needs to be secure with the OEM protecting the integrity and confidentiality of the firmware.
The other building blocks of the Cyber Resilience Act are device authentication, device identity management, device access management, data integrity, and data confidentiality - all the mechanisms to achieve the requirements that exist today. None of them are new technologies, it is just following good practices when it comes to a secure design.